
In the old days before cloud computing, the IT department was expected to be responsible for securing everything located behind their firewall including the hardware, virtualization system, operating system, and applications. In the era of cloud computing, IT can no longer have complete responsibility, the new IT model is called the “shared security model” as described by Azure, AWS, OCI, and GCP.
In a shared security model, responsibility is now divided between “the things IT must secure” and “the things the cloud vendor must secure”. It is important in a shared security model, to not assume that being on the cloud is automatically more secure, it is as secure as the IT department makes it in terms of the things IT must secure in this new model.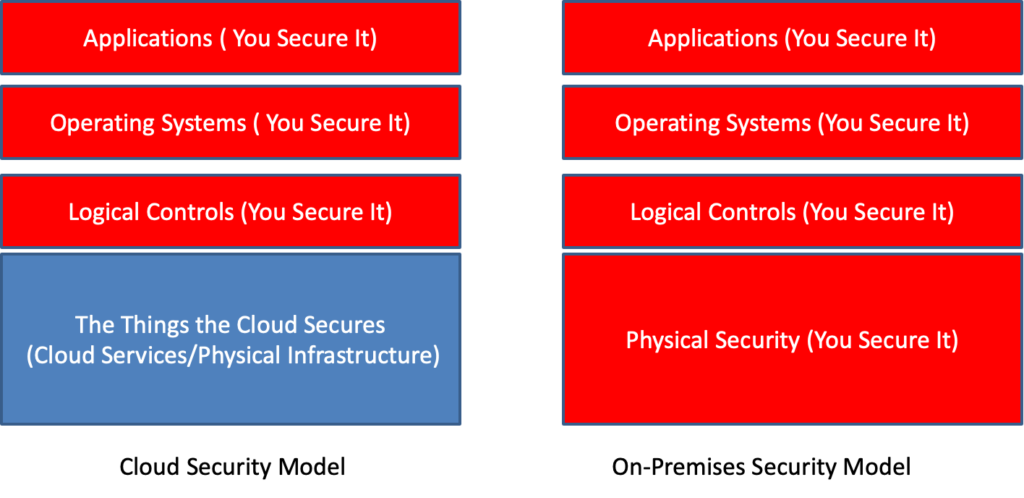
The Things You Must Secure
Cloud systems can be made highly secure through proper configuration, however one doesn’t need the NSA to tell you cloud breaches are widely prevalent in the news nearly every month due to cloud misconfiguration from human error. While one could argue the cloud vendors could do a better job of making it harder to shoot yourself in the foot, the good news is the cloud security configuration is still largely the responsibility of the IT department to control and monitor just like on-prem, and risks can largely be mitigated through following the specific security best practices of your cloud vendor.
The Things the Cloud Vendor Must Secure.
A growing challenge in recent times is the huge growth in cloud services offered by the major cloud vendors has increased the probability of hitting a cloud vendor security issue you can’t control or fix as part of the shared security model.
For example, the following are recent issues that would have allowed access to other tenants utilizing these impacted cloud services, or similar severity issue.
June 2024 – Azure – Managed Azure SQL Authentication Bypass – Trend Micro revealed authentication to Managed Azure SQL can be bypassed without authentication.
Nov 2022 – AWS AWS AppSync – DataDog showed they could bypass the service’s cross-account role usage validations and take action as the service across other customer accounts.
Sept 2022 – OCI Attache-Me. – Vulnerability in Oracle Cloud Infrastructure (OCI) would allow unauthorized access to cloud storage volumes of all users, violating cloud isolation
June 2022 – OCI CVE-2022-2150 – Exploitable vulnerability allows a high privileged attacker with network access to compromise Oracle Cloud Infrastructure.
March 2022 – Azure AutoWarp was a critical vulnerability in the Azure Automation service that allowed unauthorized access to other Azure customer accounts using the Azure Automation service.
January 2022 – AWS Glue Vulnerability enabled one to access data owned by other AWS Glue customers, though no customer data was impacted.
Sept 2021 – Azure ChaosDB allowed access to the Cosmos DB databases of Microsoft Azure customers, though no evidence was this was used before being closed, at least one major CAE ISV cloud utilizes Cosmos DB in their design.
Sept 2021 – Azurescape would have allowed a malicious Azure to execute code on other users’ containers, steal customer secrets and images deployed to the platform.
Sept 2021 – Azure OMI An issue in a Microsoft agent in Azure Linux VM’s that had a remote code execution as root.
NOTE: There was no evidence according to the cloud vendors that their customer data was stolen from these now closed issues.
TotalCAE Platform does not use any of the above services, by design we utilize the smallest set of cloud services for our SaaS to function (mainly to ensure portability across all infrastructure providers) which has a side effect of reducing exposure to these types of vulnerabilities. Using defense in depth can protect against some of these, and focusing on the risks you can control in the shared security model of the cloud.
Last updated 06/7/2024
